Open Source: How to maximize Open Source Software safely
Turn OSS Security & License Risks into Innovation
Learn about:
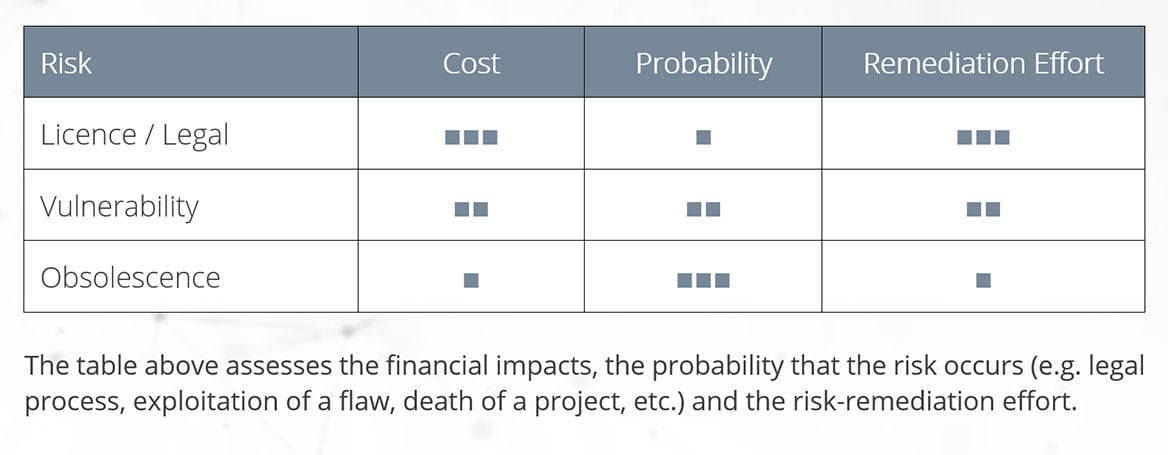
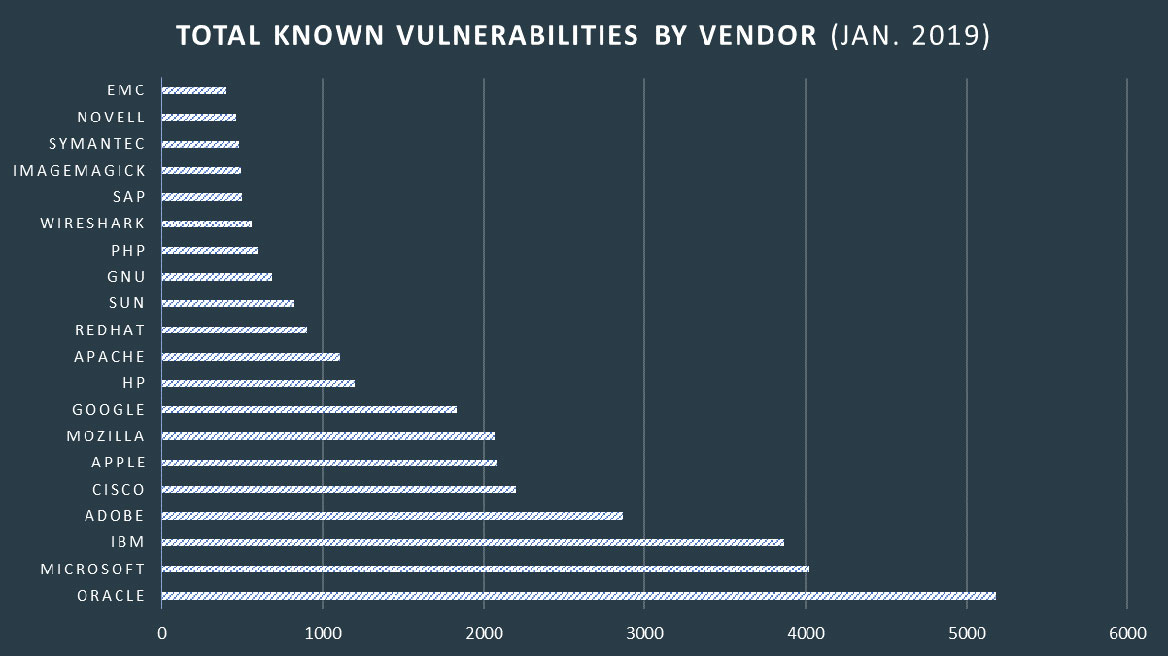
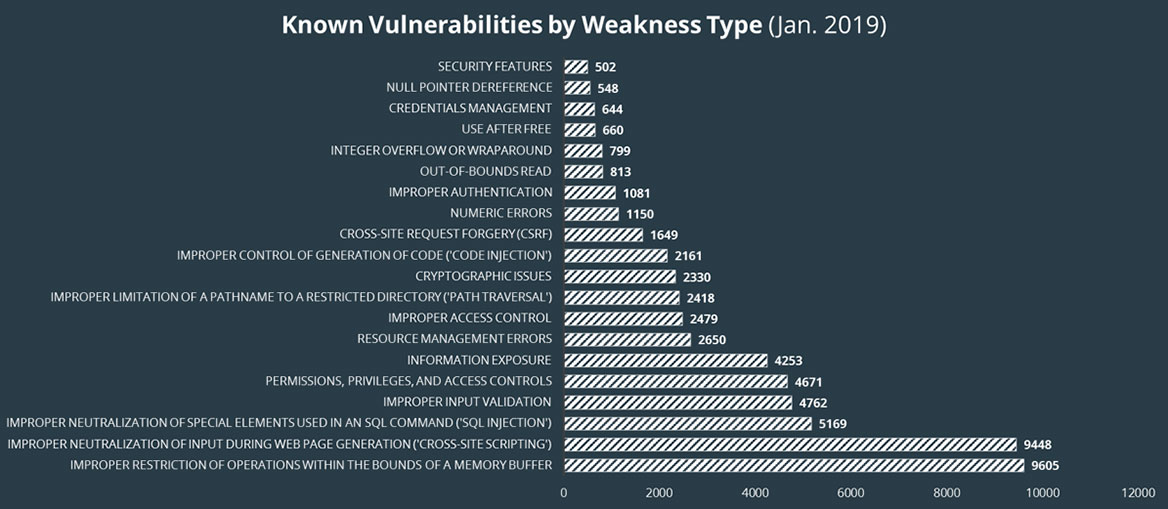
- The three types of risks you may be exposed to associated with open source software
- The potential Impact of these risks on your enterprise
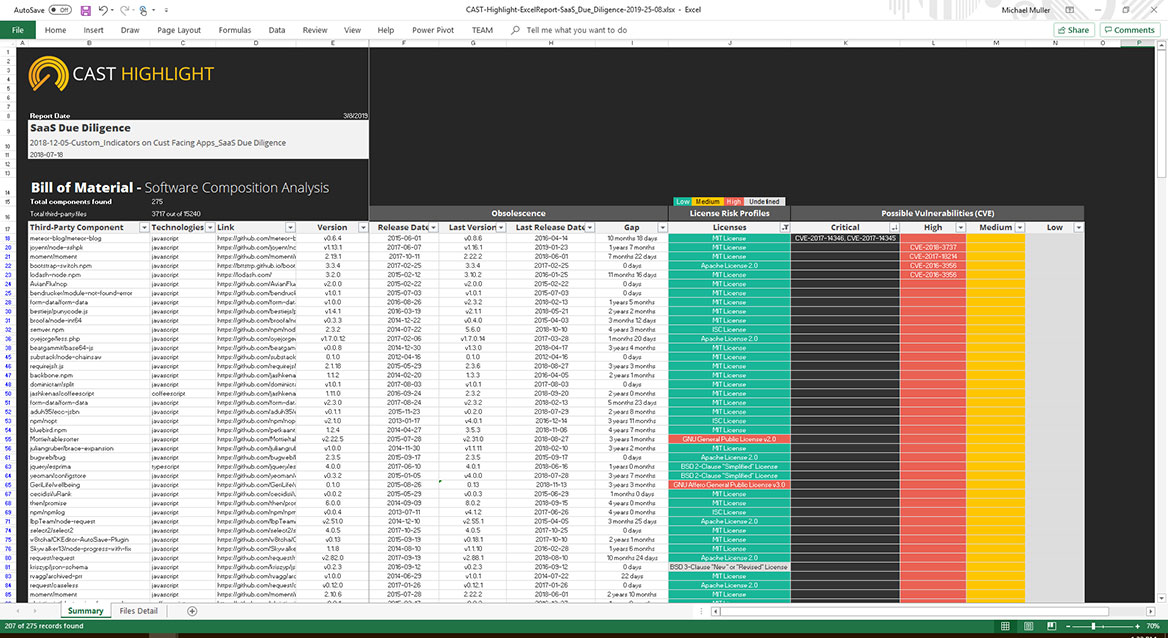
- The best practices to manage and mitigate these risks